vSAN provides feature to encrypt the data at rest. Below are pre-requisites to enable vSAN encryption –
- You will need a Key Management Server (KMS)
- vCenter should establish a trusted connection with the KMS server and vice versa
- User should have privileges on vCenter :
Host.Inventory.EditCluster
Cryptographer.ManageEncryptionPolicy
Cryptographer.ManageKMS
Cryptographer.ManageKeys
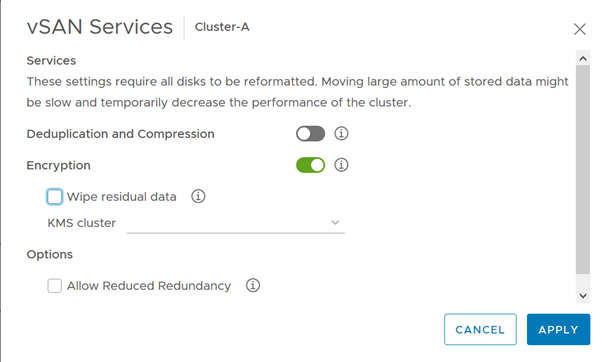
To enable encryption, Go to cluster -> Configure tab -> vSAN -> Services -> Encryption
Important vSAN Encryption terminologies :-
- KMIP : Key Management Interoperability Protocol :-
- A standard protocol that clients use to talk to KMS.
- The KMIP 1.1 protocol is required for use with vSAN Encryption
2. KMS : Key Management Server :-
- Key management is a core requirement for using vSAN Encryption and VM Encryption.
- A Key Management Solution using Key Management Interoperability Protocol (KMIP) version 1.1 is required.
3. KEK: Key Encryption Key :-
- The key encryption key (KEK) is stored in KMS.
- Each vSAN cluster has one KEK.(per-tenant key)
- Key Encryption Keys are AES-256 compatible
4. DEK: Data Encryption key :-
- Data Encryption key (DEK) is the key used in the I/O path to encrypt/decrypt data.
- DEKs are XTS-AES-256 keys.
- Each disk in a vSAN disk group will have a unique DEK.
5. HEK: Host Encryption Key :-
- This is similar to the KEK, but is used to encrypt vSAN host core dumps, not data.
- All hosts in a vSAN cluster use the same HostKey.
- Using a Host Key, customers can safely send encrypted core dumps to VMware Global Support without disclosing DEKs.
- The HEK assists in maintaining the integrity of customer data, while assisting VMware Global Support with problem resolution.
- vSAN Host Keys are AES-256
6. Key cache :-
- A vSphere Host kernel module that caches the KEK from the KMS for use by vSAN Encryption and VM Encryption.